No embedded device manufacturers would claim that the exposure of connected devices to security threats is due to vulnerabilities in the security components available on the market today. This would be ridiculous: it is easy to find specialist components such as secure elements or high-end systems-on-chip (SoCs) which will implement sophisticated forms of cryptography, secure on-chip key storage, power analysis and other security functions. Properly integrated into system designs, these components provide a strong shield for the device which hosts them.
So if security components are readily available, why do successful attacks on embedded, connected devices continue on a daily basis? After all, the evidence of cyber attacks on electronics systems is abundant. Independent research shows that the number of cyber attacks on IoT devices in the US surged by 300% in 2019 compared to a year earlier. At the same time, it is estimated that some 57% of US IoT devices are vulnerable to attacks of a medium or high severity, and that each breach of an IoT end-point costs on average $9m.
The financial cost of a successful cyber attack is due not only to the loss of revenue caused by service outage. Other costs include damage to the product manufacturer's brand, potential penalties from government authorities for breaching security regulations, and the diversion of skilled and expensive engineering resources from productive development work to urgent recovery and repair measures. Regulation in this area also continues to tighten, forcing IoT device manufacturers to pay attention to compliance requirements. The EU's Cybersecurity Act and China's Cybersecurity Law impose wide-ranging requirements backed by independent testing of device vulnerability, while the California Consumer Privacy Act imposes fines of $2,500 on companies for each unintentional violation.
But despite all these costs and rules, compromised end-points remain vulnerable. In some cases, this will be because of a vulnerability in some part of the system beyond the secure element or secure SoC. Most commonly, such a vulnerability is in a standard external Flash memory storing critical code or data.
In other cases, a device is exposed to cyber attack because the system has no secure element or secure SoC, and so lacks the sophisticated protection that it would provide.
In both cases, the barriers to the implementation of hardware-level security are generally cost and difficulty. And it is true that high-end, payment-grade security components aimed at financial products such as payment terminals and mobile phones are technically complex and difficult for engineers who are not security specialists to implement.
But now a new generation of secure Flash memory products has come on to the market to provide a secure hardware foundation for embedded devices which do not require payment-grade protection. Often featuring a standard Flash memory package footprint and pin-out, and controlled via the standard SPI NOR Flash instruction set, these secure Flash memories are easy for general embedded device designers to implement, but provide a comprehensive set of security functions to protect connected devices from attack on a system's integrity or data privacy.
Why implement security in a memory device?
It's traditional to conceive of non-volatile memory as a simple device: bits are written to it, and the same bits are then read out. It's generally thought of as a store, not a processor.
In fact, of course, every NOR Flash memory used for code or application data includes logic to control memory operations and communications with the host via a serial peripheral interface. Secure Flash devices build on and extend this logic block to provide security functions alongside the memory control functions.
Flash memory manufacturers such as Winbond have developed this new generation of secure Flash products because of the limitations of the embedded Flash memory provision in microcontrollers and SoCs. While advanced microcontrollers and SoCs have migrated to wafer fabrication processes at nodes smaller than 20nm, the scaling of embedded NOR Flash has not followed suit. This means that in the latest MCUs and SoCs, the embedded floating-gate flash process is not available and the capacity is often not large enough to store the sophisticated software code which they are intended to run.
So in today's embedded device designs, application code is more commonly stored in an external Flash memory device. But if the device is connected - particularly if it is an IoT device connected to the internet - the boot code in external Flash is vulnerable to attack, and data is vulnerable to theft or intrusion, unless the memory device itself is shielded by comprehensive security functionality. This is the value of a secure Flash device, complementary to SoC/MCU security
The key capabilities of secure Flash
The reason for replacing standard external NOR Flash in an IoT end-point with secure Flash, then, is to protect the integrity of boot code and application data. Various secure Flash devices on the market provide some form of secure storage. At its most basic, this security functionality provides for secure, encrypted authentication: this means that the Flash device will only permit the authorised host to perform Read and Write operations, protecting the data from being accessed by any device other than the host SoC.
But this provides only a limited form of security protection. To protect against the many types of cyber attack, and to provide for compliance with regulations such as the EU Cybersecurity Law's Basic and Substantial levels of security functionality, Winbond has developed a multi-function secure NOR Flash memory, the W77Q, part of its TrustME family of secure Flash products. In addition to secure authentication, the W77Q provides: -*Resilience: protection, detection and recovery, to ensure that an IoT device can automatically reboot into known safe code even after a cyber attack has attempted to disable it
*Root-of-trust to enable authenticated communication with the host SoC and with external systems such as cloud computing services.
*Secure data storage
*Secure channel from Flash to a trust authority in the cloud for over-the-air firmware updates. This channel means that the memory can update to a new version of boot code independently of the SoC, and even when the SoC has itself been compromised.
The W77Q has been assessed by an external, accredited laboratory. It complies with the requirements of the EU's GDPR privacy legislation, and provides the 'Substantial' level of protection as specified by the EU's Cybersecurity Act. It holds security certifications including CC EAL2 (VAN.2), IEC62443, SESIP and the Arm Platform Security Architecture (PSA) certification.
Resilience is particularly important for IoT devices - and is a capability missing from most secure Flash products. In some devices, such as utility meters, physical intrusion (tampering) is a common form of attack for which protection is required. Large, very valuable assets such as power generation plants or military bases might be subject to physical intrusion into a local area network.
For IoT devices, however, the main threat is a scalable cyber attack exploiting a remote connection via the internet to the entire population of installed devices. The US National Institute of Standards and Technology's (NIST) SP 800-193 standard specifies mechanisms which protect firmware and configuration data from such attacks, and which can detect and recover from successful attacks. The W77Q provides the resilience functions required to conform to this standard. Resilience has three elements: protection against attack, detection of attacks, and recovery from attack
Functions such as encrypted authentication to prevent attempts by unauthorized devices to access data provide protection against attack. An attack might be successfully carried out on the host SoC, however, so the W77Q maintains the ability to detect when an attack has taken place. For instance, it checks that stored code has not been corrupted automatically, whenever the code is updated or accessed. It can also scan code on the instruction of the host device.
If the W77Q detects that an attack has been successful and that, for instance, the compromised, authentic SoC has corrupted its own boot code, the Flash device automatically and with proper authentication recovers the platform firmware. It does so via its 'Safe Fallback' function, which reinstates boot code to a known safe version. This Safe Fallback function is backed by an authenticated watchdog timer, which can force the host SoC into a clean boot using the known safe code.
Winbond's approach in developing the W77Q has been to provide an off-the-shelf set of layered security capabilities to enable easy deployment by customers. With the W77Q, Winbond provides:
*End-to-end, out-of-the-box security, with no need for prior security expertise
*Fast deployment
*A complete solution backed by compatible products from security software vendors
*Simple security certification
*Affordability.
By providing this comprehensive set of capabilities in a familiar SPI NOR Flash package with a standard footprint, Winbond can help ensure that no IoT device needs to go to market without proper protection against cyber attack.
(Note: The author of this article, Hung-Wei Chen, is director of Security Solution Marketing and Application Division at Winbond Electronics.)
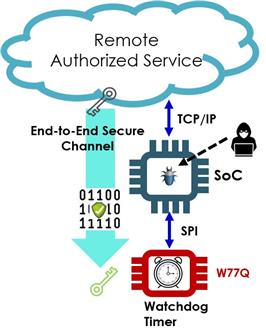
The W77Q can institute a secure channel to a trust centre in the cloud for over-the-air software updates even when the host SoC has been compromised. (Image credit: Winbond)
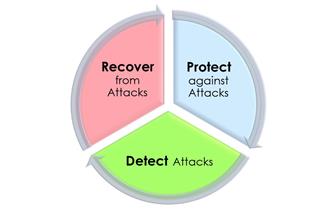
The W77Q can always be trusted to maintain platform health by protection, detection and recovery. (Image credit: Winbond)
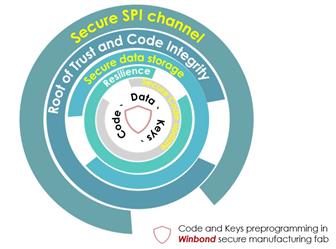
Comprehensive protection Comprehensive protection against cyber attacks requires the implementation of a layered set of security capabilities. (Image credit: Winbond)
DIGITIMES' editorial team was not involved in the creation or production of this content. Companies looking to contribute commercial news or press releases are welcome to contact us.